
- •Single-User License Agreement
- •Chapter 1: Design Goals of USB
- •Chapter 2: The Big Picture
- •Chapter 3: Cables and Connectors
- •Chapter 4: USB Cable Power Distribution
- •Chapter 5: LS/FS Signaling Environment
- •Chapter 6: LS/FS Transfer Types & Scheduling
- •Chapter 7: Packets & Transactions
- •Chapter 8: Error Recovery
- •Chapter 9: USB Power Conservation
- •Chapter 10: Overview of HS Device Operation
- •Chapter 11: The High-Speed Signaling Environment
- •Chapter 12: HS Transfers, Transactions, & Scheduling
- •Chapter 13: HS Error Detection and Handling
- •Chapter 14: HS Suspend and Resume
- •Chapter 15: HS Hub Overview
- •Chapter 16: 2.0 Hubs During HS Transactions
- •Chapter 17: 2.0 Hubs During LS/FS Transactions
- •Chapter 18: Configuration Process
- •Chapter 19: USB Device Configuration
- •Chapter 20: Hub Configuration
- •Chapter 21: Device Classes
- •Chapter 22: Overview of USB Host Software
- •Appendix A: Standard Device Requests
- •Appendix B: Hub Requests
- •Appendix C: Universal Host Controller
- •Appendix D: Open Host Controller
- •About This Book
- •The MindShare Architecture Series
- •Cautionary Note
- •Specifications This Book is Based On
- •Organization of This Book
- •Part One: Overview of USB 2.0
- •Part Two: Low- & Full-Speed Device Operation
- •Part III: High-Speed Device Operation
- •Part IV: USB 2.0 Hub Operation with LS/FS/HS Devices
- •Part VI: USB Software Overview
- •Appendices
- •Who Should Read this Book
- •Prerequisite Knowledge
- •Documentation Conventions
- •Hexadecimal Notation
- •Binary Notation
- •Decimal Notation
- •Bits Versus Byte Notation
- •Identification of Bit Fields (logical groups of bits or signals)
- •Visit Our Web Page
- •We Want Your Feedback
- •Shortcomings of the Original PC I/O Paradigm
- •Limited System Resources
- •Interrupts
- •I/O Addresses
- •Non-shareable Interfaces
- •End User Concerns
- •Cable Crazed
- •Installation and Configuration of Expansion Cards
- •No Hot Attachment of Peripherals
- •Cost
- •The USB Paradigm
- •Enhanced System Performance
- •Hot Plug and Play Support
- •Expandability
- •Legacy Hardware/Software Support
- •Low Cost
- •Summary of Key USB Features
- •How to Get the USB Specifications
- •2 The Big Picture
- •Overview
- •USB 1.x Systems and Devices
- •Low-Speed and Full-Speed Devices
- •How Transactions Are Generated
- •What the Descriptors Contain
- •How the Transfer Descriptors Are Fetched
- •Frame Generation
- •Sharing the Bus
- •Bandwidth Consideration Summary
- •2.0 Systems and Devices
- •Low-Speed and Full-Speed Devices in a 2.0 System
- •Example 2.0 Host Controller Support for LS/FS Devices
- •High-Speed Devices in a 2.0 System
- •High-Speed Devices Attached to 1.x Ports
- •High-Speed Transactions and Microframe Generation
- •High-Speed Bandwidth Summary
- •The Players
- •USB Client Drivers
- •USB Bus Driver
- •USB Host Controller Driver
- •USB Host Controller/Root Hub
- •The Host Controller
- •The Root Hub
- •USB Hubs
- •Hub Controller
- •Hub Repeater
- •Hub’s Role in Configuration
- •USB Devices
- •High-Speed Devices
- •Full-Speed Devices
- •Low-Speed Devices
- •USB Communications Model
- •Communications Flow
- •Transfers, IRPs, Frames, and Packets
- •Transfers
- •The USB Driver, IRPs, and Frames
- •The Host Controller Driver and Transactions
- •The Host Controller and Packets
- •Device Framework (how devices present themselves to software)
- •Device Descriptors
- •Device Framework
- •USB Bus Interface Layer
- •USB Device Layer
- •Function Layer
- •USB Peripheral Connection
- •Full-Speed Hubs
- •High-Speed Hubs
- •High-Speed Devices
- •Topology
- •The Connectors
- •Series A Connectors
- •Series B Connectors
- •Cables
- •Low-Speed Cables
- •Cable Power
- •Electrical and Mechanical Specifications
- •USB Power
- •Hubs
- •Current Budget
- •Over-Current Protection
- •Voltage Drop Budget
- •Power Switching
- •Bus-Powered Hubs
- •Power During Hub Configuration
- •Bus-Powered Hub Attached to 500ma Port
- •Bus-Powered Hub Attached to 100ma Port
- •Bus-Powered Hub Attached to Port with >100ma but <500ma
- •Current Limiting
- •Bus-Powered Devices
- •Low-Power Devices
- •High-Power Devices
- •Power During Configuration
- •Insufficient Port Power
- •Self-Powered Hubs
- •Power During Configuration
- •Locally Powered Bus Interface
- •Hybrid Powered Device
- •Current Limiting
- •Self-Powered Devices
- •Power During Configuration
- •Locally Powered Bus Interface
- •Hybrid Powered Device
- •Overview
- •Detecting Device Attachment and Speed Detect
- •Full-Speed Device Connect
- •Low-Speed Device Connect
- •Detecting Device Disconnect
- •Bus Idle
- •Device RESET
- •Differential Signaling
- •Differential Drivers
- •Full-Speed Drivers
- •Low-Speed Drivers
- •Hub Driver Characteristics
- •Differential Receivers
- •Start of Packet (SOP)
- •End of Packet (EOP)
- •Single-Ended Receivers
- •NRZI Encoding
- •Bit Stuffing
- •Summary of USB Signaling States
- •Overview
- •Client Initiates Transfer
- •Communications Pipes
- •Communication Initiated by I/O Request Packets
- •Frame-Based Transfers
- •Transfer Types
- •Isochronous Transfers
- •Direction of Transfers
- •Service Period
- •Bandwidth Allocation
- •Error Recovery
- •Establishing Synchronous Connections
- •The Problem with Isochronous Transfers
- •The Feedback/Feed Forwarding Solution
- •Synchronization Types
- •Source/Sink Combinations and Synchronization Methods
- •How Endpoints Report Their Synchronization Capabilities
- •Feedback Data
- •Association Between Data Endpoint and Feedback Endpoint
- •Interrupt Transfers
- •Service Period
- •Bus Bandwidth Allocation
- •Error Recovery
- •Control Transfers
- •Bus Bandwidth Allocation
- •Error Recovery
- •Bulk Transfers
- •Bus Bandwidth Allocation
- •Error Recovery
- •Overview
- •Packets — The Basic Building Blocks of USB Transactions
- •Synchronization Sequence
- •Packet Identifier
- •Packet-Specific Information
- •Cyclic Redundancy Checking (CRC)
- •End of Packet (EOP)
- •Token Packets
- •SOF Packet
- •IN Packet
- •OUT Packet
- •SETUP Packet
- •Data Packets — DATA0 and Data1
- •Handshake Packets
- •Preamble Packet
- •Transactions
- •IN Transactions
- •IN Transaction Without Errors
- •IN Transaction with Errors
- •IN Transaction with No Interrupt Pending/Target Busy
- •IN Transaction with Target Stalled
- •IN Transaction During Isochronous Transfer
- •OUT Transactions
- •OUT Transaction Without Data Packet Errors
- •OUT Transaction with Errors
- •OUT Transaction — Target Unable to Accept Data
- •OUT Transaction With Target Stalled
- •OUT Transaction During Isochronous Transfer
- •Setup Transactions/Control Transfers
- •Two Stage Control Transfer
- •Three Stage Control Transfer with IN Data Stage
- •Three Stage Control Transfer with OUT Data Stage
- •Control Transfers With Errors
- •8 Error Recovery
- •Overview
- •Packet Errors
- •PID Checks
- •CRC Errors
- •Bit Stuff Errors
- •Packet-Related Error Handling
- •Token Packet Errors
- •Data Packet Errors
- •Handshake Packet Errors
- •Bus Time-Out
- •False EOPs
- •False EOP During Host Transmission
- •False EOP During Target Transmission
- •Data Toggle Errors
- •Data Toggle Procedure Without Errors
- •Data Toggle during OUT Transactions
- •Data Toggle During IN Transactions
- •Data Toggle Procedure with Data Packet Errors
- •Data Toggle and Data Packet Errors — OUT Transactions
- •Data Toggle and Data Packet Errors — IN Transactions
- •Data Toggle With Handshake Packet Error — IN Transaction
- •Special Case: Data Toggle During Control Transfer
- •Babbling Devices
- •Loss of Activity (LOA)
- •Babble/LOA Detection and Recovery
- •Frame Timer
- •Host to Hub Skew
- •Hub Repeater State Machine
- •Isochronous Transfers (Delivery Not Guaranteed)
- •Interrupt Transfer Error Recovery
- •Bulk Transfer Error Recovery
- •Control Transfer Error Recovery
- •Power Conservation — Suspend
- •Device Response to Suspend
- •Hub Response to Suspend
- •Global Suspend
- •Initiating Global Suspend
- •Resume from Global Suspend
- •Resume Initiated by Host
- •Remote Wakeup from Device
- •Remote Wakeup via Hub Port Event
- •Selective Suspend
- •Initiating Selective Suspend
- •Resume from Selective Suspend
- •Host Initiated Selective Resume
- •Selective Wakeup from Device
- •Selective Suspend When Hub is Suspended
- •Device Signals Resume
- •Port Receives Connect or Disconnect
- •Selective Suspend Followed by Global Suspend
- •Resume via Reset
- •Hub Frame Timer After Wakeup
- •Overview
- •New High-Speed Device Features
- •1.x USB Device Support
- •The 2.0 Host Controller
- •Overview
- •Detecting High-Speed Device Attachment
- •Initial Device Detection
- •Device Reset and the Chirp Sequence
- •High-Speed Interfaces Idled
- •High-Speed Differential Signaling
- •Impedance Matching
- •High-Speed Driver Characteristics
- •High-Speed Idle
- •High-Speed Differential Receivers
- •High-Speed Driver/Receiver Compliance Testing
- •Activating Test Mode
- •The Test Setup
- •Eye Pattern Tests
- •High-Speed Start of Packet & Synchronization Sequence
- •High-Speed End of Packet (EOP)
- •Detection of High-Speed Device Removal
- •High-Speed RESET and Suspend
- •Signaling RESET
- •Signaling Suspend
- •Differentiating Between RESET and Suspend
- •Overview
- •High-Speed Transaction Scheduling
- •Microframes
- •Theoretical HS Bandwidth
- •Periodic Transfers
- •High-Speed Isochronous Transfers
- •Maximum Packet Size
- •Isochronous Bandwidth/Performance
- •Isochronous Transaction Errors
- •High-Speed Interrupt Transfers
- •Maximum Packet Size
- •Interrupt Bandwidth
- •Interrupt Transaction Errors
- •High-Bandwidth Transactions
- •Detecting High-Bandwidth Endpoints and Packet Size
- •Isochronous High-Bandwidth Scheduling and Protocol
- •High Bandwidth Interrupt Transactions
- •High Bandwidth Throughput
- •Non-Periodic Transfers
- •High-Speed Bulk Transfers
- •Maximum Packet Size
- •Bulk Bandwidth
- •Bulk Transactions Errors
- •High-Speed Control Transfers
- •High-Speed Control Bandwidth
- •Ping Transactions
- •The Problem
- •The Solution
- •The Ping Protocol
- •Overview
- •High-Speed Bus Time-out
- •False EOP
- •HS Babbling Device Detection
- •Overview
- •Entering Device Suspend
- •Device Resume
- •15 HS Hub Overview
- •Overview
- •USB 2.0 Hub Attached to High-Speed Port
- •High-Speed Transactions
- •USB 2.0 Hub Attached to Full-Speed Port
- •Overview
- •High-Speed Hub Repeater
- •Receiver Squelch
- •Re-clocking the Packet
- •Port Selector State Machine
- •Elasticity Buffer
- •The Repeater State Machine
- •Overview
- •The Structure of Split Transactions
- •Isochronous Split Transaction Examples
- •Example Split Isochronous OUT Transaction
- •Example Split Isochronous IN Transaction
- •Example Split Transactions with Data Verification
- •Split OUT Sequence
- •Split IN Sequence
- •The Split Token Packet
- •The Transaction Translator
- •The Major Elements of the Transaction Translator
- •High-Speed Handler
- •Periodic Transfer Start-Split Buffer
- •Periodic Complete-Split Buffer
- •Bulk/Control Buffers
- •Low-Speed/Full-Speed Handler
- •Split Transaction Scheduling
- •Split Transaction Scheduling Example
- •SOF Packets
- •Host Delivers Isochronous Start Split
- •Host Delivers Interrupt Start Split
- •Host Issues Complete-Split to Fetch Isochronous IN Data
- •Host Fetches Interrupt OUT Completion Status
- •Host Continues to Fetch Isochronous IN Data
- •Transaction End
- •High-Speed Scheduling Can Include Other Transactions
- •Single versus Multiple Transaction Translators
- •Periodic Split Transactions
- •Periodic Split Transaction Pipeline
- •High Speed Handler Receives Start Split
- •Start-Split Buffer
- •Low-Speed/Full-Speed Handler
- •Complete-Split Buffer
- •Isochronous OUT Split Transaction Sequence
- •Isochronous OUT Start Split
- •Handling CRC16 During Split Isochronous OUT Transactions
- •Isochronous IN Split Transaction Sequence
- •Isochronous IN Start Split
- •Isochronous IN Complete Split
- •Handling CRC16 During Split Isochronous IN Transactions
- •Interrupt Split OUT Transaction Sequence
- •Interrupt OUT Start Split Sequence
- •Interrupt OUT Complete Split Sequence
- •Interrupt IN Split Transaction Sequence
- •Interrupt IN Start Split Sequence
- •Interrupt IN Complete Split Sequence
- •Handling CRC16 During Split Interrupt IN Transactions
- •Non Periodic Split Transactions
- •Non-Periodic Split Transaction Pipeline
- •High Speed Handler
- •Non-periodic Buffers
- •Low-/Full-Speed Handler
- •Bulk/Control Split OUT Transaction Sequence
- •Bulk/Control OUT Start Split Sequence
- •Bulk/Control OUT Complete Split Sequence
- •Bulk/Control Split IN Transaction Sequence
- •Bulk/Control IN Start Split Sequence
- •Bulk/Control IN Complete Split Sequence
- •Overview
- •The Configuration Software Elements
- •USB Host Controller Driver
- •Configuration Software
- •Default Control Pipe
- •Resource Management
- •Device Client Software
- •Root Hub Configuration
- •Each Device Is Isolated for Configuration
- •Reset Forces Device to Default Address (zero)
- •Host Assigns a Unique Device Address
- •Host Software Verifies Configuration
- •Power Requirements
- •Bus Bandwidth
- •Configuration Value Is Assigned
- •Client Software Is Notified
- •Overview
- •Summary of Configuration Process
- •How Software Detects Device Attachment & Speed
- •Polling the Status Change Endpoint
- •Getting Port Status
- •Resetting the Port
- •Reading and Interpreting the USB Descriptors
- •The Standard Descriptors
- •How Software Accesses the Descriptors
- •Device Descriptor
- •Class Code Field
- •Maximum Packet Size Zero
- •Manufacturer, Product, Serial Number
- •Number of Configurations
- •Device Qualifier Descriptor
- •Configuration Descriptors
- •Number of Interfaces
- •Configuration Value
- •Attributes and Maximum Power
- •Other Speed Configuration Descriptor
- •Interface Descriptors
- •Interface Number and Alternate Setting
- •Number of Endpoints
- •Interface Class and Subclass
- •Protocol
- •Endpoint Descriptors
- •Device States
- •Attached State
- •Powered State
- •Default State
- •Addressed State
- •Configured State
- •Suspend State
- •Client Software Configuration
- •Configuring the Hub
- •The Default Pipe
- •The Status Change Pipe
- •Reading the Hub’s Descriptors
- •1.x Hub Descriptors
- •Hub’s Standard Device Descriptor
- •Hub Configuration Descriptor
- •Number of Interfaces
- •Configuration Value
- •Maximum Bus Power Consumed
- •Hub Interface Descriptor
- •Status Endpoint Descriptor
- •Status Change Endpoint Address/Transfer Direction
- •Transfer Type
- •Maximum Data Packet Size
- •Polling Interval
- •Hub Class Descriptor
- •Power Switching Mode Implemented
- •Compound Device or Hub Only
- •Over-Current Protection Mode
- •Power On to Power Good Delay
- •Maximum Bus Current for Hub Controller
- •Device Removable/Non-removable
- •Port Power Mask
- •High-Speed Capable Hub Descriptors
- •Descriptors When Hub Is Operating at Full Speed
- •The 2.0 Hub’s Class-Specific Descriptor
- •Powering the Hub
- •Checking Hub Status
- •Detecting Hub Status Changes
- •Reading the Hub Status Field
- •Reading Port Status
- •Enabling the Device
- •Summary of Hub Port States
- •21 Device Classes
- •Overview
- •Device Classes
- •Audio Device Class
- •Standard Audio Interface Requirements
- •Synchronization Types
- •Audio Class-Specific Descriptors
- •Audio Class-Specific Requests
- •Communications Device Class
- •Communications Device Interfaces
- •Communications Class-Specific Descriptors
- •Communications Class-Specific Requests
- •Display Device Class
- •The Standard Display Device Class Interface
- •Display Device-Specific Descriptors
- •Device-Specific Requests
- •Mass Storage Device Class
- •Standard Mass Storage Interface
- •Control Endpoint
- •Bulk Transfer Endpoints
- •Interrupt Endpoint
- •General Mass Storage Subclass
- •CD-ROM Subclass
- •Tape Subclass
- •Solid State Subclass
- •USB Software
- •Function Layer
- •Device Layer
- •Interface Layer
- •The Software Components
- •USB Driver (USBD)
- •Configuration Management
- •USB Elements Requiring Configuration
- •Allocating USB Resources
- •Verifying Power
- •Tracking and Allocating Bus Bandwidth
- •Bus Bandwidth Reclamation
- •Data Transfer Management
- •Providing Client Services (The USB Driver Interface)
- •Pipe Mechanisms
- •Client Pipe Requirements
- •Command Mechanisms
- •Appendix
- •Overview
- •Standard Device Requests
- •Set/Clear Feature
- •Device Remote Wakeup
- •Endpoint Stall
- •Set/Get Configuration
- •Set/Get Descriptor
- •Set/Get Interface
- •Get Status
- •Device Status
- •Self-Powered Bit
- •Remote Wakeup Bit
- •Port Test Bit
- •Endpoint Status
- •Sync Frame
- •Device Tests
- •High-speed Driver/Receiver Compliance Testing
- •Activating Test Mode
- •Overview
- •Hub Request Types
- •Standard Requests and Hub Response
- •Hub Class Requests
- •Get/Set Descriptor Request
- •Get Hub Status Request
- •Hub Status Fields
- •Local Power Status
- •Over-Current Indicator
- •Hub State Change Fields
- •Local Power Status Change
- •Over-Current Indicator Change
- •Set/Clear Hub Feature Request
- •Hub Local Power Change Request
- •Hub Over-Current Change Request
- •Get Port Status Request
- •Port Status Fields
- •Current Connect Status Field
- •Port Enabled/Disabled
- •Suspend
- •Over-Current Indicator
- •Reset
- •Port Power
- •Low-Speed Device Attached
- •High-Speed Device Attached
- •Port Test
- •Port Indicator Control
- •Port Change Fields
- •Current Status Change
- •Port Enable/Disable Change
- •Suspend Change (Resume Complete)
- •Over-Current Indicator Change
- •Reset Complete
- •Set/Clear Port Feature
- •Port Test Modes
- •Get Bus State
- •Overview
- •Universal Host Controller Transaction Scheduling
- •Universal Host Controller Frame List Access
- •UHC Transfer Scheduling Mechanism
- •Bus Bandwidth Reclamation
- •Transfer Descriptors
- •Queue Heads
- •UHC Control Registers
- •Overview
- •Open Host Controller Transfer Scheduling
- •The Open Host Controller Transfer Mechanism
- •The ED and TD List Structure
- •Interrupt and Isochronous Transfer Processing
- •Control and Bulk Transfer Processing
- •The Done Queue
- •Interrupt Transfer Scheduling
- •Endpoint Descriptors
- •Transfer Descriptors
- •General Transfer Descriptor
- •Isochronous Transfer Descriptor
- •The Open Host Controller Registers
- •Index
Chapter 7: Packets & Transactions
Figure 7-24: OUT Transaction During Isochronous Transfer
OUT Packet |
|
|
|
Data Packet |
|
|
||||
|
|
from Host |
|
|
|
to USB Device |
|
|
||
Sync |
|
OUT Token |
|
EOP |
|
Sync |
|
Data Packet (up to 1023 bytes |
|
EOP |
|
|
|
|
|
||||||
|
|
|
|
|
|
|
|
|
|
|
Isochronous endpoint does not return a handshake pack et
Setup Transactions/Control Transfers
Control transfers are used to issue commands (also called requests) to USB devices. For example, control transfers are performed during USB device configuration to read the standard descriptors and assign a unique address to a device. Control transfers always begin with a setup transaction, called the setup stage. The setup stage defines the nature of the control transfer. Some control transfers include a data stage consisting of one or more IN or OUT transactions that are used to deliver the payload of the control transfer. Whether data is sent to or received from the device is defined by the setup stage. The final stage of a control transfer is the status stage. This stage confirms that the requested operation has been completed successfully. Control transfers exist in two basic forms:
•Transfers consisting of a setup stage and status stage.
•Transfers consisting of a setup stage, data stage, and status stage.
The data phase of a setup transaction contains 8 bytes of information as defined in Table 7-3. This information defines the request being issued to the device and provide all the information needed by the device to fulfill the request.
163

USB System Architecture
Table 7-3: Format of Setup Transaction Data Phase
Offset |
Field |
Size |
Value |
|
Description |
|
|
|
|
|
|
|
|
|
|
|
|
0 |
Request- |
1 |
Bit-map |
Characteristics of Request |
|
|
Type |
|
|
D7 |
Data xfer direction |
|
|
|
|
|
0 = Host to device |
|
|
|
|
|
1 = Device to host |
|
|
|
|
D6:5 |
Type |
|
|
|
|
|
0 = Standard |
|
|
|
|
|
1 = Class |
|
|
|
|
|
2 = Vendor |
|
|
|
|
|
3 = Reserved |
|
|
|
|
D4:0 |
Recipient |
|
|
|
|
|
0 = Device |
|
|
|
|
|
1 = Interface |
|
|
|
|
|
2 = Endpoint |
|
|
|
|
|
3 = Other |
|
|
|
|
|
4:31 = Reserved |
|
|
|
|
|
|
1 |
Request |
1 |
Value |
Specific Request. |
|
|
|
|
|
|
|
2 |
Value |
2 |
Value |
Word-sized field that varies according |
|
|
|
|
|
to request. |
|
|
|
|
|
|
|
4 |
Index |
2 |
Index or |
Word-sized field that varies according |
|
|
|
|
Offset |
to request. Typically used to pass an |
|
|
|
|
|
index or offset. |
|
|
|
|
|
|
|
6 |
Length |
2 |
Count |
Number of bytes to transfer if there is a |
|
|
|
|
|
data stage required for this transfer. |
|
|
|
|
|
|
|
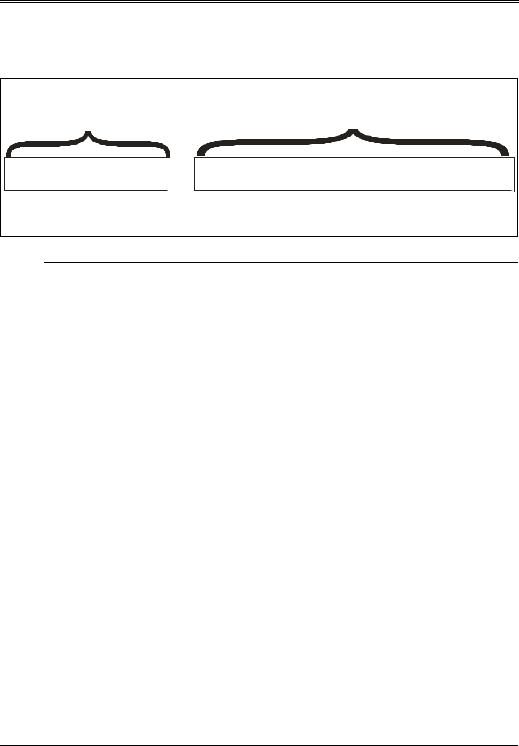
Two Stage Control Transfer
A two stage control transfer consists solely of the setup and status stages as illustrated in Figure 7-25. In this instance the 8 bytes delivered during the setup transaction contains all the information needed to perform the specified request (e.g., remote wake-up request). The status stage consists of an IN transaction to verify that the request has been successfully processed.
164
Chapter 7: Packets & Transactions
Figure 7-25: Format of a Two Stage Control Transfer
|
6HWXS 6WDJH |
|
|
6WDWXV 6WDJH |
|
|
6HWXS 7UDQ |
|
|
,1 7UDQVDFWLRQ |
|
|
|
|
V |
|
|
VHWXS |
E\WHV |
DFN |
,1 |
E\WHV |
DFN |
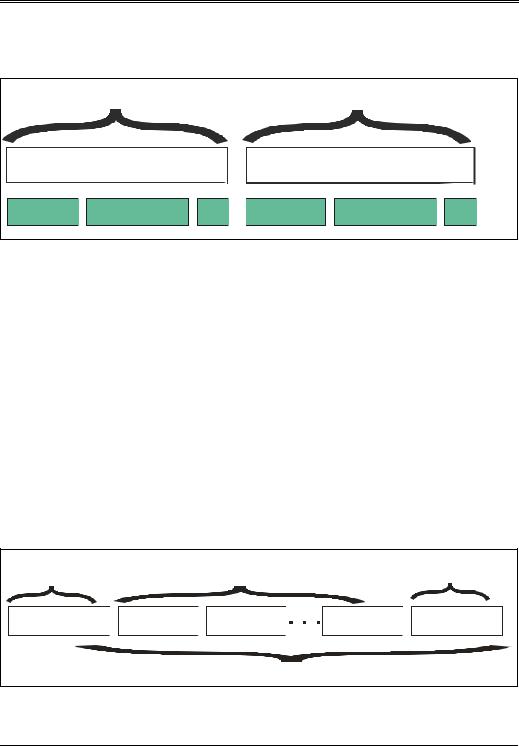
Three Stage Control Transfer with IN Data Stage
Figure 7-26 illustrates a control transfer that requires data be returned from the target device back to the host. As an example, a control transfer may be performed when the host system issues a request to read a device descriptor. The first stage of the transfer consists of the setup transaction that defines the nature of the control transfer. The setup transaction consists of the setup token, data packet, and handshake. During setup transactions data is always sent to the target device to specify the type of request. Following the setup phase, the host initiates one or more IN transactions, prompting the target to return the requested data. The host completes the control transfer by using an OUT transaction to request verification that the device endpoint has successfully returned the contents of the descriptor. Note that the target device indicates successful completion of the request by issuing an ACK handshake during the OUT transaction. The OUT data packet issued by the host has a length of zero.
Figure 7-26: Control Transfer Requesting Data from Target
Setup Stage |
|
Data Stage (one or more IN transactions) |
|
Status Stage |
||||
Setup Transaction |
|
IN Transaction |
|
IN Transaction |
|
IN Transaction |
|
OUT Transaction |
|
|
|
|
|||||
|
|
|
|
|
|
|
|
|
Three Stage Read Control Transfer
165
USB System Architecture
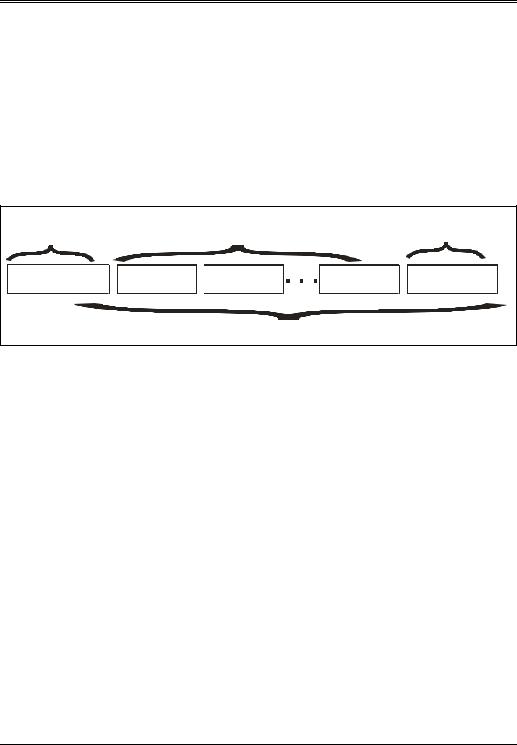
Three Stage Control Transfer with OUT Data Stage
Figure 7-27 illustrates the format of a control transfer in which a command is issued to a control endpoint. The setup transaction defines the request being issued and is followed by the data stage (one or more OUT transactions). The host then issues an IN token to the control endpoint to obtain completion status. The target returns a data packet with a length of zero to indicate that it has successfully processed the initial control request.
Figure 7-27: Control Transfer Issuing a Command to a Target’s Control Endpoint
Setup Stage |
Data Stage (one or more OUT transactions |
Status Stage |
) |
||
Setup Transaction |
OUT Trans. |
OUT Trans. |
OUT Trans. |
IN Transaction |
|
|
Three Stage Write Control Transfer |
|
|
||
Control Transfers With Errors
The host system attempts retries to ensure that a control transfer completes successfully. The action taken by the target and host depends on the nature of the error condition and when the error occurs during the transfer. See Chapter 8, entitled "Error Recovery," on page 167 for further details.
166
