
- •47 Cellular radio systems
- •47.1 Introduction
- •47.2 Principles of operation
- •47.2.1 Network configuration
- •47.2.2 Signalling
- •47.2.3 Location registration
- •47.2.4 Call set up
- •47.2.6 Power control
- •47.3 Radio planning
- •47.3.1 Cell repeat patterns
- •47.3.3 Radio propagation
- •47.3.4 Practical radio planning
- •47.3.5 Adding capacity
- •47.4 Overview of systems
- •47.4.2 Tacs
- •47.5 Detailed description of gsm
- •47.5.1 Gsm architecture
- •47.5.2 Air interface
- •47.5.3 Speech coding and channel coding
- •47.5.4 Gsm signalling
- •47.5.5 Security features
- •47.5.6 Gsm services and features
- •47.5.7 Roaming
- •47.6 Services
- •47.6.1 Supplementary services
- •47.6.2 Value added services
- •47.6.3 Data services
- •47.7 Future developments
- •47.7.1 Microcells
- •47.7.2 Intelligent networks
- •47.7.3 Personal communications
- •47.8 Conclusion
47.5.5 Security features
The information on the air interface needs to be protected, to provide user data (including speech) confidentiality and to prevent fraudulent use of subscriber and mobile identities. The basic mechanisms employed are user authentication and user data encryption. Each mobile user is provided with a Subscriber Identity Module (SIM) which contains the IMSI, the individual subscriber authentication key (Ki) and the authentication algorithm (A3). After the mobile user has made an access and service request, the network checks the identity of the user by sending a random number (RAND) to the mobile. The mobile uses the RAND, Ki and A3 algorithm to produce a signed response SRES. This response is compared with a similar response calculated by the network, and access only continues if the two responses match.
The SIM also contains a cipher key generating algorithm (A8). The MS uses the RAND and A8 to calculate a ciphering key (Kc) which is used to encrypt and decrypt signalling and user data information.
The authentication centre (AUC) is responsible for all security aspects and its function is closely linked with the HLR. The AUC generates the Ki's and associates them with IMSIs, and provides the HLR with sets of RAND, SRES and Kc for each IMSI. The HLR then provides the appropriate VLR with these sets and it is the VLR which carries out the authentication check. Authentication of mobile users can be carried out on call set up, both mobile originated and mobile terminated, on location updating, and on activation of supplementary services. As the authentication sets are used up in the VLR, further sets are requested from the HLR.
An additional security feature of GSM is the equipment identity register (E1R). This enables monitoring of the mobile equipment 1MEI (International Mobile Equipment Identity) which is used to validate mobile equipments thus preventing non-approved, faulty or stolen equipment from using the system. This range of security features provide a high degree of protection to the user and the network operator.
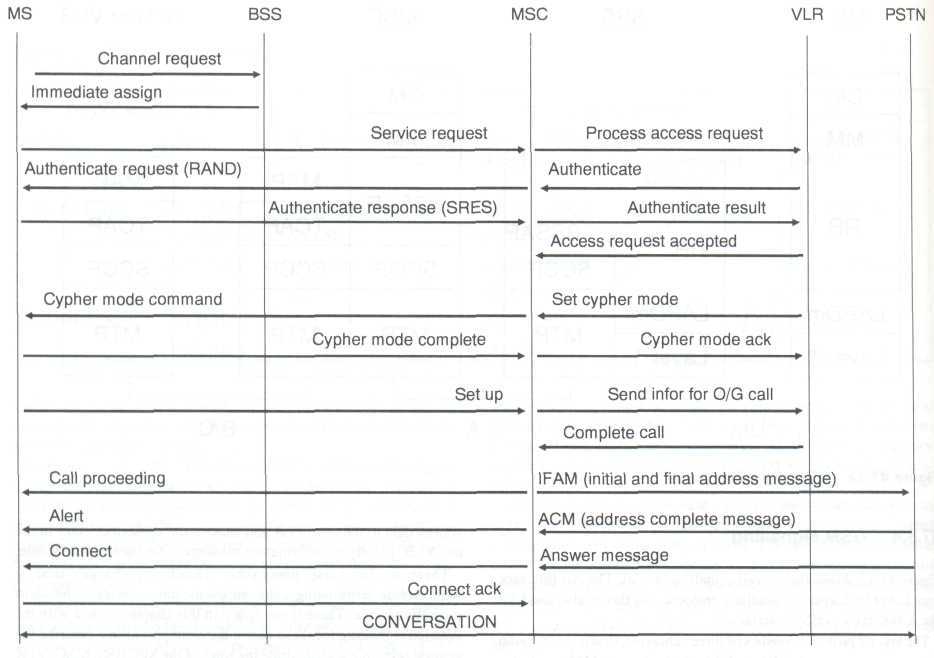
Figure 47.13 Mobile originating call
47.5.6 Gsm services and features
In addition to speech, GSM offers a wide range of data bearer services up to 9.6kbit/s suitable for connection to circuit switched or packet switched data networks. GSM also supports Group 111 facsimile as a data service by use of an appropriate converter.
A comprehensive range of supplementary services are offered by GSM, including call forwarding, call barring, multi-party service, advice of charge and others. A full description is provided in the GSM Recommendations, and further detail of cellular services is provided later in this chapter.
An important feature of GSM is the short message service (SMS). This allows transmission of alphanumeric messages of up to 160 characters to or from a mobile via a service centre. If the message cannot be delivered due to mobile being switched off, or outside of the coverage area, the message is stored at a service centre and re-transmitted when the mobile registers again. Received messages can be displayed on the mobile and stored in the SIM for future reference. A related service is cell broadcast which allows messages of up to 93 characters to be sent to all mobiles within a specific geographical area, for example to deliver traffic or weather reports.
