
- •Computer Basics
- •Applications: Word Processing
- •Word Processing
- •Steps to produce a document
- •Features/Terms:
- •Do it! Simple Text
- •Directions:
- •Move the cursor:
- •Features/Terms:
- •Features/Terms:
- •Applications: Desktop Publishing
- •Features/Terms:
- •Instant Messaging
- •Applications: Security & Utility
- •Security Programs
- •Types of security programs:
- •Utility Programs
- •Examples:
- •Integrated Software
- •Computer Types & Applications: Summary
- •Input: Intro
- •Types of Input
- •Keyboard
- •Common differences:
- •Input: Keyboard
- •Explanation:
- •Input: Pointing Devices
- •Input: Terminals
- •Input: Multimedia
- •Voice Input
- •Input: Data Automation
- •Input: Data Accuracy
- •Input: Summary
- •Input: Quiz
- •Processing: cpu
- •Explanation:
- •Processing: Motherboard
- •Processing: Summary
- •Output: Printer Types
- •Impact Printers
- •Types of Impact Printers
- •Types of Non-Impact Printers
- •Thus, Things to Consider When Choosing a Printer:
- •Output: Summary
- •Storage: Accessing Data
- •Total time to transfer a kilobyte:
- •Don't lose it!
- •Storage: Caring for Data
- •What are the risks?
- •First: a Back Up Plan
- •Storage: Summary
- •Computer to Computer: Transmission Media
- •Broadcast
- •Computer to Computer: Modems Signals
- •Transmission Rate
- •Physical Types
- •Digital Modems
- •Types of Digital Modems
- •How Device Speeds Compare
- •Protocols
- •Computer to Computer: Summary
- •System Software: Types
- •More Terms
- •Common Operating Systems for Desktop Computers
- •Life Cycle
- •Which is most popular?
- •Wikipedia:
- •Hitslink.Com:
- •System Software: Utilities
- •Security Software
- •Malware: What you need protection from
- •Programs that add protection:
- •Programming: Summary
- •What You See: On the Front
- •Explanation:
- •What You See: Summary
Applications: Security & Utility
There are many categories of special purpose programs that are generally called Utility Programs. Some of these just tweak the user interface and some perform highly technical tasks.
The Security Programs that help keep the bad guys from messing with your computer and its data are the most important type of utility program.
Security Programs
To do a good job of keeping your computer safe from random visitors or from crime syndicates, you need several types of programs.
Types of security programs:
Anti-malware: Continuously watches for incoming attacks. Scans regularly for hidden malware (a virus, trojan, worm or other intrusive software). Repairs many kinds of damage. Anti-virus is the old name for these programs but current versions deal with much more than just computer viruses.
Firewall: Controls who gets into your computer from the Internet or other network connection.
Anti-spam: Examines incoming email and sends known or suspected bad messages to a special folder, Spam or Junk.
Purpose: |
|
Major Advantage: |
|
Major Disadvantage: |
|
Examples of security programs, some of which include several programs: Norton Security Suite, Microsoft Security Essentials, Avira AntiVirus, Windows Firewall, Norton 360, Trend Micro Internet Security Plus, Zone Alarm
Utility Programs
There are many categories of utility programs, including security software. What is counted as a utility program depends on who is doing the counting! The usual definition is that a utility program is not application software that the user uses to create something, like a document or image, nor is it a game or a browser. It does something to way the computer looks or behaves, often in the background. [Some web sites that sell software include a lot more in their Utility category, including games(!), money management software, genealogy software, course management software, and many more.]
Over time, features and services that used to be available only through a utility program get included in the operating system or as part of the program the program was designed to modify. Nothing changes more and faster than the world of computers!
Purpose: |
|
Major Advantage: |
|
Major Disadvantage: |
|
Examples:
Parental control programs block access (especially for children) to web sites that are not suitable or are more likely to result in malware attacks - NetNanny, K9 Web Protection, some operating systems include some features.
Encryption programs encode your data so that to read it the user must have the right key code. Some operating systems include some type of encryption. Could be for the whole disk, selected folders, or selected files.
Password management software remembers all of your logon and password information so that you only have to remember how to get into the password software - one thing! The file that records your passwords is encrypted - Password Safe, Roboform, KeePass.
Back-up and file synchronization software can automatically save a copy of your data or the whole computer's contents to DVDs, tape, or to a data site online. To be prepared in case a disaster happens, whether it is a security issue or a dead hard drive issue, you need a back-up copy of your important data - Windows Backup & Restore, Norton 360, Norton Ghost. Online file storage - Carbonite. File storage with synchronization: Dropbox, Box, Microsoft Skydrive, Google Drive
Disk defragmenting software rearranges files so that all parts of the file are next to each other. The computer will scatter pieces of a file all over the disk, wherever there is some room. Defragmenting makes it easier for the computer to find and display the file - Windows Disk Defragmenter, Norton SpeedDisk.
See System Software: Utilities for more discussion.
Applications: PIM
A PIM program (Personal Information Management) is a special kind of database. A PIM will normally include an address book, a calendar to schedule activities and appointments, and a to-do list where you list chores, calls to make, various things to do.
Some popular programs which include PIM functions are Microsoft Office Outlook, Lotus Organizer, Windows Calendar and Windows Contact List, Google Calendar and Google Notebook, Palm Desktop, Novell Groupwise.
New versions of these programs add email management, wireless access, and other features for the new, hot technologies. The new goal for a PIM seems to be to vanish into the background, while letting you have access to your email, calendar, and scheduling software from anywhere.
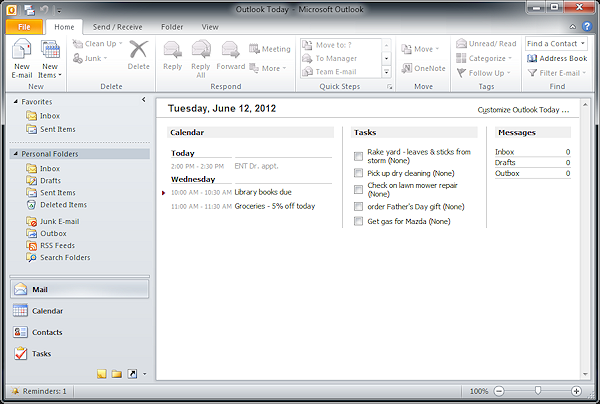
Example of a PIM: Microsoft Outlook
Purpose: |
|
Major Advantage: |
|
Contact Manager
An advanced PIM may be called a Contact Manager. Such a program is optimized to make it easy to track who you have talked to or met with and what you did or said.
A contact manager automatically links a name in the address book to names in the calendar. Clicking on the name in the calendar brings up the full contact information, including fields for notes about what you did and reminders for what you need to do after the meeting or conversation. From the address book you can bring up a list of when you had contacts with this person. Powerful stuff!
Applications: Integrated & Suites
